RFC 4408 deals with concatenating multiple TXT records for longer SPF entries, but DNS label limits (63 characters per label, 253 total for FQDN) seem to be a separate constraint of the DNS system.
Could you clarify how ENS is using RFC 4408 techniques to address the DNS label length issue? Or did you mean TXT values and not DNS labels?
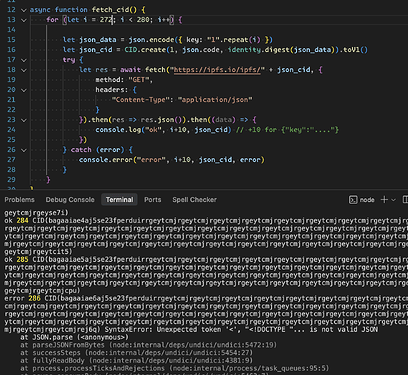
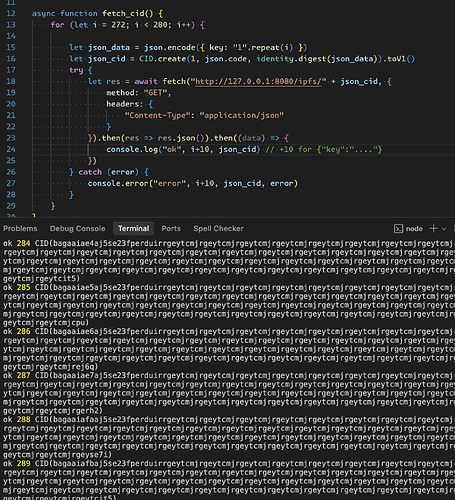
I was able to reproduce problem you describe.
Took the longest sample CID from dag-cbor-test-data.sol and prepended f to it to make it base16 CIDv1. Opening it locally works fine, but indeed, the URL https://ipfs.io/ipfs/f0171008206a663726177d82a5892000171008c01a36a7368613235362e747874d82a58250001551220a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e6c6964656e746974792e747874d82a50000155000b48656c6c6f20576f726c646d6b656363616b3235362e747874d82a58250001551b20592fa743889fc7f92ac2a37bb1f5ba1daf2a5c84741ca0e0061d243a2e6707ba646a736f6ed82a589e000171009801a36b7368613235362e6a736f6ed82a582600018004122065a4c4ca5acfc4bf3b34e138c808730f6c9ce141a4c6b889a9345e66c9739d736d6964656e746974792e6a736f6ed82a570001800400117b2248656c6c6f223a22576f726c64227d6e6b656363616b3235362e6a736f6ed82a5826000180041b20068cd05557eb0a2358c3fab33bcecc929f0b4f01caed8562f772bbeb8869eec9666e6573746564d82a59014800017100c202a263726177d82a5892000171008c01a36a7368613235362e747874d82a58250001551220a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e6c6964656e746974792e747874d82a50000155000b48656c6c6f20576f726c646d6b656363616b3235362e747874d82a58250001551b20592fa743889fc7f92ac2a37bb1f5ba1daf2a5c84741ca0e0061d243a2e6707ba646a736f6ed82a589e000171009801a36b7368613235362e6a736f6ed82a582600018004122065a4c4ca5acfc4bf3b34e138c808730f6c9ce141a4c6b889a9345e66c9739d736d6964656e746974792e6a736f6ed82a570001800400117b2248656c6c6f223a22576f726c64227d6e6b656363616b3235362e6a736f6ed82a5826000180041b20068cd05557eb0a2358c3fab33bcecc929f0b4f01caed8562f772bbeb8869eec96a696e6465782e68746d6cd82a581900015500143c68313e48656c6c6f20576f726c643c2f68313e6a726561646d652e747874d82a50000155000b48656c6c6f20576f726c646b636f6e6669672e6a736f6ed82a570001800400117b2248656c6c6f223a22576f726c64227d produces HTTP 502.
I’ve confirmed the Error 502 is produced by NGINX and not IPFS backend (Rainbow), but I’m hesitant investigating further, as the use case looks like a misuse of identity multihashes which should be only used for small data leaves (see questions below).
What is a.. “dynamic” CID? I’m honestly puzzled by the mention of “dynamic cidv1” - CIDs by definition represent immutable content.
Are you perhaps using CIDs as containers for the data itself (via identity hash) rather than as true cryptographic hash functions and real verifiable content identifiers? This feels like an inefficient way of abusing the system.
The example CID above is a CBOR document inlined inside of a CID with identity multihash (cid inspector):
$ ipfs dag get f0171008206a663726177d82a5892000171008c01a36a7368613235362e747874d82a58250001551220a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e6c6964656e746974792e747874d82a50000155000b48656c6c6f20576f726c646d6b656363616b3235362e747874d82a58250001551b20592fa743889fc7f92ac2a37bb1f5ba1daf2a5c84741ca0e0061d243a2e6707ba646a736f6ed82a589e000171009801a36b7368613235362e6a736f6ed82a582600018004122065a4c4ca5acfc4bf3b34e138c808730f6c9ce141a4c6b889a9345e66c9739d736d6964656e746974792e6a736f6ed82a570001800400117b2248656c6c6f223a22576f726c64227d6e6b656363616b3235362e6a736f6ed82a5826000180041b20068cd05557eb0a2358c3fab33bcecc929f0b4f01caed8562f772bbeb8869eec9666e6573746564d82a59014800017100c202a263726177d82a5892000171008c01a36a7368613235362e747874d82a58250001551220a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e6c6964656e746974792e747874d82a50000155000b48656c6c6f20576f726c646d6b656363616b3235362e747874d82a58250001551b20592fa743889fc7f92ac2a37bb1f5ba1daf2a5c84741ca0e0061d243a2e6707ba646a736f6ed82a589e000171009801a36b7368613235362e6a736f6ed82a582600018004122065a4c4ca5acfc4bf3b34e138c808730f6c9ce141a4c6b889a9345e66c9739d736d6964656e746974792e6a736f6ed82a570001800400117b2248656c6c6f223a22576f726c64227d6e6b656363616b3235362e6a736f6ed82a5826000180041b20068cd05557eb0a2358c3fab33bcecc929f0b4f01caed8562f772bbeb8869eec96a696e6465782e68746d6cd82a581900015500143c68313e48656c6c6f20576f726c643c2f68313e6a726561646d652e747874d82a50000155000b48656c6c6f20576f726c646b636f6e6669672e6a736f6ed82a570001800400117b2248656c6c6f223a22576f726c64227d | jq
{
"config.json": {
"/": "bagaaiaarpmreqzlmnrxseorck5xxe3deej6q"
},
"index.html": {
"/": "bafkqafb4nayt4sdfnrwg6icxn5zgyzb4f5udcpq"
},
"json": {
"/": "bafyqbgabunvxg2dbgi2tmltkonxw5wbklataaamaaqjcazneytffvt6ex45tjyjyzaehgd3mttqudjggxce2snc6m3exhhltnvuwizlooruxi6jonjzw63wyfjlqaamaaqabc6zcjbswy3dpei5cev3pojwgiit5nzvwky3dmfvtenjwfzvhg33o3avfqjqaagaaigzaa2gnavkx5mfcgwgd7kztxtwmskpqwtybzlwykyxxok56xcdj53eq"
},
"nested": {
"/": "bafyqbqqcujrxeylx3avfreqaafyqbdabunvhg2dbgi2tmltupb2nqksyeuaacvisecszdjwubp2caqckaeltht5xwginmldfx4f43izlk6zhpwnnt4kg43djmrsw45djor4s45dyotmcuuaaafkqac2imvwgy3zak5xxe3denvvwky3dmfvtenjwfz2hq5gyfjmckaabkunsawjpu5byrh6h7evmfi33wh23uhnpfjoii5a4udqamhjehixgob52mrvhg33o3avfrhqaafyqbgabunvxg2dbgi2tmltkonxw5wbklataaamaaqjcazneytffvt6ex45tjyjyzaehgd3mttqudjggxce2snc6m3exhhltnvuwizlooruxi6jonjzw63wyfjlqaamaaqabc6zcjbswy3dpei5cev3pojwgiit5nzvwky3dmfvtenjwfzvhg33o3avfqjqaagaaigzaa2gnavkx5mfcgwgd7kztxtwmskpqwtybzlwykyxxok56xcdj53eq"
},
"raw": {
"/": "bafyqbdabunvhg2dbgi2tmltupb2nqksyeuaacvisecszdjwubp2caqckaeltht5xwginmldfx4f43izlk6zhpwnnt4kg43djmrsw45djor4s45dyotmcuuaaafkqac2imvwgy3zak5xxe3denvvwky3dmfvtenjwfz2hq5gyfjmckaabkunsawjpu5byrh6h7evmfi33wh23uhnpfjoii5a4udqamhjehixgob52"
},
"readme.txt": {
"/": "bafkqac2imvwgy3zak5xxe3de"
}
}
I feel I am missing something.
Mind elaborating why you do this inlining for high level directory listings, and not using real IPFS blocks and short CIDs that work everywhere and do not require wasting bandwidth sending entire data back and forth (once to server, and once back)?
![]() from namesys.eth
from namesys.eth![]()